The Diverse World of Cybersecurity Teams
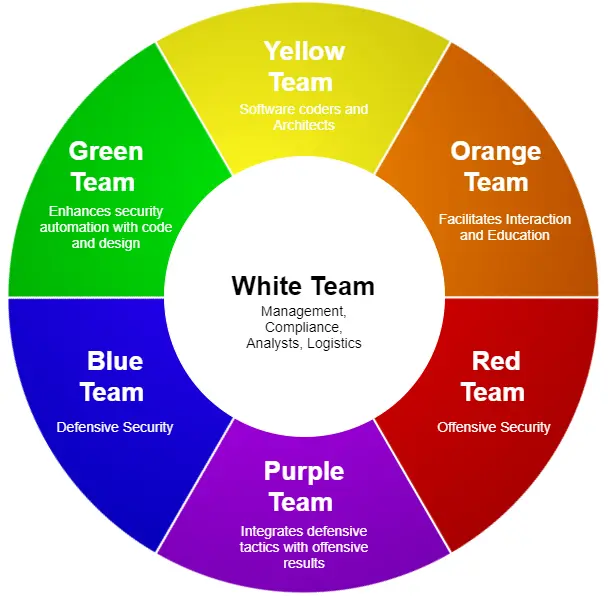
In the ever-evolving landscape of cybersecurity, organizations face a constant battle against cyber threats. To defend their assets, they rely on skilled cybersecurity teams, each equipped with unique approaches and expertise. Like the colors of a rainbow, these teams represent various perspectives and play critical roles in safeguarding digital assets. In this blog, we’ll delve into the world of cybersecurity teams and explore the strengths and specialties of the Red, Blue, Purple, Orange, Yellow, Green, and White teams.
The Red Team
The Red Team is the aggressor, simulating cyberattacks to identify vulnerabilities in an organization’s defenses. Their main objective is to find weaknesses before malicious actors do. Red Team members employ ethical hacking techniques to launch attacks such as penetration testing, social engineering, and network exploitation. Their findings help organizations patch vulnerabilities and enhance their security posture.
The Blue Team
On the other side of the spectrum is the Blue Team, responsible for defense and incident response. They focus on monitoring networks, identifying potential threats, and swiftly responding to security incidents. Blue Team members use tools like SIEM (Security Information and Event Management) to detect and mitigate attacks. Their ability to identify and neutralize threats is crucial in minimizing the impact of security breaches.
The Purple Team
The Purple Team is a combination of the Red and Blue Teams, emphasizing collaboration and information-sharing. In essence, they facilitate communication between the offensive and defensive teams, ensuring that both sides benefit from each other’s insights. By working together, they can develop more comprehensive security strategies and ensure the organization is better prepared to face sophisticated threats.
The Orange Team
The Orange Team focuses on threat intelligence and proactive threat hunting. They gather data from various sources, including cyber threat intelligence feeds, to understand the tactics, techniques, and procedures used by potential adversaries. This information allows them to preemptively adjust security measures and proactively seek out potential threats before they become imminent risks.
The Yellow Team
In contrast to the Red Team’s offensive approach, the Yellow Team focuses on creating robust security awareness training programs. They educate employees about cybersecurity best practices, the importance of strong passwords, recognizing phishing attempts, and other security-related topics. The Yellow Team plays a pivotal role in building a security-conscious culture within the organization, reducing the likelihood of successful social engineering attacks.
The Green Team
The Green Team is the sustainability arm of the cybersecurity effort. They concentrate on ensuring that the organization’s cybersecurity practices adhere to industry standards, regulations, and compliance requirements. Green Team members continually assess the organization’s security posture, conduct audits, and make recommendations to maintain compliance and minimize risk.
The White Team
Last but not least, the White Team oversees security assessments and exercises to evaluate the overall effectiveness of the cybersecurity program. They coordinate simulated cyber incidents and red teaming exercises to stress-test the organization’s defenses. The White Team’s findings and recommendations drive continuous improvement in the organization’s cybersecurity capabilities.
Conclusion
The cybersecurity landscape is complex and ever-changing, requiring a multi-faceted approach to protect valuable assets. Each color-coded cybersecurity team has its unique role, and they work in synergy to ensure a robust defense against cyber threats. The Red Team tests the organization’s vulnerabilities, the Blue Team stands guard, the Purple Team fosters cooperation, the Orange Team hunts for threats, the Yellow Team educates employees, the Green Team ensures compliance, and the White Team assesses and improves overall security.
In this vibrant rainbow of cybersecurity teams, collaboration, communication, and continuous improvement are the keys to success. By understanding and appreciating the contributions of each team, organizations can build a strong cybersecurity strategy that protects against the diverse array of threats that exist in the digital realm. Contact ITAdOn for your cybersecurity consultation.






